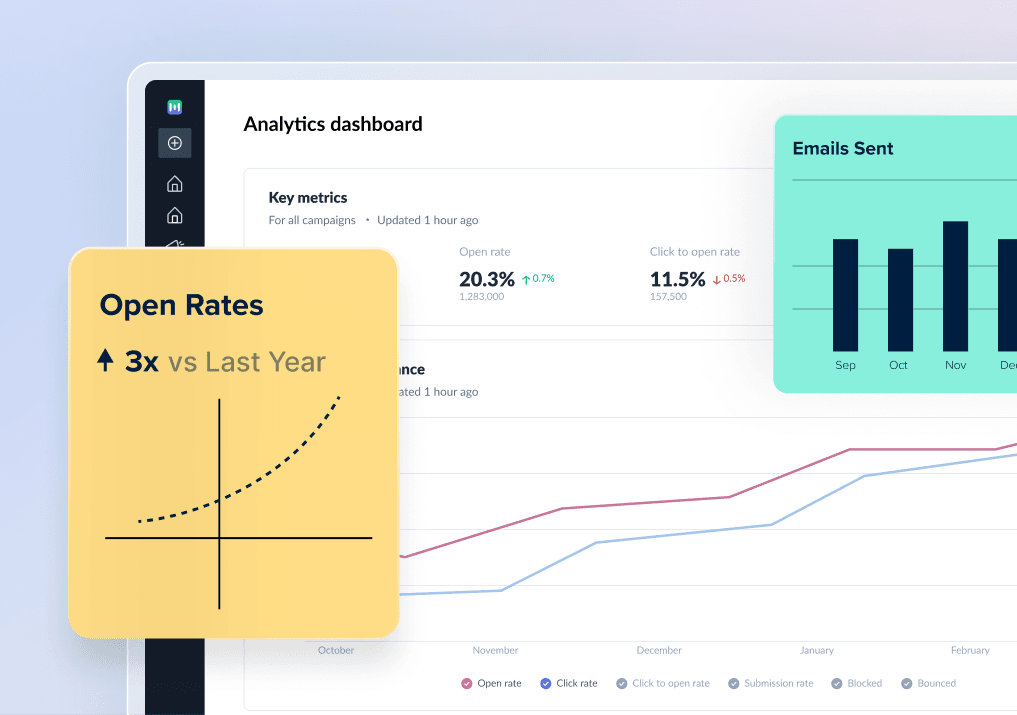
Best Multi Factor Authentication Software in 2023
Are you looking for a Multi Factor Authentication Software for your business? You have come to the right page. This guide will help you discover the best Multi Factor Authentication Software of 2023 and along with a deep dive into their features, pricing, rating, etc.


What is Multi Factor Authentication Software?
Multi Factor Authentication software provides an extra layer of security for accessing sensitive data by requiring multiple forms of authentication, such as passwords, biometric identification, or smart cards. This helps prevent unauthorized access to secure systems and reduces the risk of identity theft, data breaches, and other cyber threats. Companies can implement MFA solutions to protect against security vulnerabilities and ensure compliance with industry regulations, making it an essential tool for maintaining data privacy and security.
How Multi Factor Authentication Software work or function?
Multi-factor authentication software works by requiring additional layers of authentication beyond just a password. This can include something the user knows, such as a PIN, something the user has, such as a token or smart card, or something the user is, such as a fingerprint or facial recognition. By requiring multiple factors, the software provides increased security and reduces the risk of unauthorized access. It is commonly used for online banking, remote access, and other sensitive applications.
Benefits of Multi Factor Authentication Software?
Benefits of Multi-Factor Authentication Software:
- Multi-factor authentication adds an extra layer of security to protect against unauthorized access.
- It reduces the risk of data breaches and identity theft.
- It improves compliance with regulatory requirements.
- It provides a user-friendly authentication experience for employees and customers.
- It enhances trust in online transactions and improves customer satisfaction.
- It enables remote workforce to access company systems securely.
How we curated this list
We conducted extensive research to identify a wide range of software options within each category. This involved exploring online resources, industry publications, software directories, and user reviews. Please note that the pricing and features mentioned here are subject to change. We recommend you to visit the product website for the latest information before making a decision.

#1
Google Authenticator
Product Description
Search the world's information, including webpages, images, videos and more. Google has many special features to help you find exactly what you're looking for.
Pros and Cons
- Built-in security, automatic protections, and alerts for Google Accounts help keep them safe from unauthorized access and data breaches.
- Google Password Manager helps users create strong passwords and alerts them if passwords have been compromised in a data breach.
- Sign in with Google allows users to authenticate themselves safely to thousands of sites and services across the web, while maintaining privacy controls in one place.
- Some users may not want to rely heavily on Google to manage their online security and may prefer to use third-party apps or services for security and password management.
- Users who are not comfortable with phone-based authentication or Google Prompt may find it less secure than traditional passwords.
- While Security Checkup may provide personalized recommendations to help strengthen the security of the Google Account, it may be time-consuming for users to complete the process.

#2
Microsoft Authenticator
Product Description
Protect your personal and business data from outside breaches by securely logging into your organization's applications with Microsoft's mobile authenticator app.
Pros and Cons
- Microsoft offers a range of different security solutions for different needs, such as cloud security, industrial and critical infrastructure protection, and risk management.
- The Microsoft Defender product family includes endpoint security and management solutions, and vulnerability management tools.
- Microsoft Authenticator provides a convenient and secure two-factor authentication method for online accounts.
- It can be overwhelming to navigate through the numerous product families and capabilities offered by Microsoft Security, and it may be difficult for users to determine which solutions best suit their needs.
- The cost of utilizing multiple Microsoft Security products simultaneously may be prohibitive for small and medium businesses with limited budgets.
- Some users may prefer to use third-party security solutions that offer different or additional features not available through Microsoft Security.

#3
LastPass
Product Description
Go beyond saving passwords with the best password manager! Generate strong passwords and store them in a secure vault. Now with single-sign on (SSO) and adaptive MFA solutions that integrate with over 1,200 apps.
Pros and Cons
- Convenient and secure: LastPass stores all your passwords in one place and keeps them secure with encryption and multi-factor authentication.
- Easy to use: With browser extensions and mobile apps, LastPass makes it easy to access your passwords on any device.
- Time-saving: LastPass can auto-fill your login credentials, saving you time and hassle.
- Cost: To access all the features, you'll need to pay for a premium subscription.
- Complex setup: Configuring LastPass to work with all your devices and web applications can be time-consuming.
- Security concerns: Anytime you store your passwords in one place, there is always a risk of a breach, even with LastPass's security measures.

#4
Duo Security
Product Description
Protect your workforce and user data from cybersecurity risks with Multifactor Authentication (MFA), Two-Factor Authentication (2FA) and a Single Sign-On solution.
Pros and Cons
- Duo offers a wide range of secure access solutions such as multi-factor authentication, remote access, device trust, adaptive access policies, and single sign-on, which cater to various business needs.
- Duo provides different pricing plans at various price points, ensuring businesses can choose the right coverage that fits their budget.
- Duo offers customer support and expert advice through dedicated support, knowledge base, community forum, how-to videos, and comprehensive documentation.
- Though Duo has competitive pricing, some businesses might find the pricing plans expensive, especially for larger teams.
- Duo's adaptive access policies may require technical expertise to set up, making it hard for smaller organizations with limited IT resources to use this feature effectively.
- Some users may find it challenging to navigate the solutions due to the breadth of products offered, making it hard to pick the right features to meet their business needs.

#5
Twilio Verify API
Product Description
Validate users across SMS and preferred channels at scale with the Twilio Verify API, a turnkey, passwordless authentication solution that enables seamless and secure user onboarding, reduces fraud, and optimizes delivery rates without the heavy lifting. Twilio handles all your connectivity, channels, OTP generation, and more—so you don’t have to.
Pros and Cons
- Twilio Verify API provides a highly secure multi-channel user verification solution that is equipped with Fraud Guard to prevent fraud at scale.
- The API is easy to integrate into an app with developer-first APIs and client libraries and extensive resources available in the documentation and code exchange.
- Twilio Verify is fully managed and provides flexible pay as you go pricing with no commitments.
- The benefits of Fraud Guard and other anti-fraud tools are not explicitly stated or the exact benefits of these features are not mentioned.
- The specific suite of channels and messaging formats that the API supports are not fully disclosed.
- The pricing structure for Twilio Verify API is pay-as-you-go, which may not be cost-effective for companies with a very high volume of user verifications.

#6
Salesforce Platform
Product Description
Go digital fast and empower your teams to work from anywhere. Develop scalable, custom business apps with low-code development or give your teams the tools to build with services and APIs.
Pros and Cons
Low code development platform: Salesforce Platform allows for easy and efficient app development with its low code approach, which can save time and money for businesses.
AI-powered automation: The platform's integration with Einstein GPT and data cloud allows for AI-powered automation, optimizing and personalizing customer data across all systems.
Secure and compliant: With industry-leading security, privacy, and governance tools, Salesforce Platform ensures data security and compliance with regulations.
Annual contract requirement: All per-user products require an annual contract, which may not be suitable for some businesses that prefer more flexible pricing options.
Costly plans: The pricing of Platform Plus and Heroku Enterprise Starter plans may be high for small businesses, limiting their ability to access some of the more advanced features.
Complex features: Some of the platform's features, such as system integration and data cloud, may be complex and require specialized skills to fully utilize, which can be challenging for some businesses.

#7
Uniqkey
Product Description
cutting-edge technology that replaces traditional passwords with a secure multifactor authentication system, ensuring the highest level of security for your company's sensitive information.
Pros and Cons
- Uniqkey provides advanced passwordless authentication, making it easy to use and highly secure.
- It offers multi-factor authentication to ensure high levels of security.
- Uniqkey works seamlessly across various platforms and devices.
- Its services are relatively new in the market and therefore have limited user reviews.
- The pricing for Uniqkey's services might be a little expensive for small businesses and individuals.
- Uniqkey's authentication system and process might be complex for some users to understand.

#8
IBM Security Verify
Product Description
Authenticate customers, detect fraud and protect against malicious users across all channels
Pros and Cons
- IBM Planning Analytics with Watson can help organizations make more accurate plans and forecasts without the need for a data scientist.
- IBM Watson Assistant can power virtual agents with AI, which can be helpful in providing customer support.
- IBM Consulting services can help businesses personalize experiences at scale with the help of AI, leading to increased customer satisfaction.
- The cost of IBM software may be high for small businesses or startups.
- IBM products may require a certain level of technical expertise to operate and maintain.
- Some businesses may prefer to hire a dedicated data scientist rather than rely on AI-powered software for decision making.

#9
Frontegg
Product Description
Frontegg is an end-to-end user management platform for B2B SaaS, powering strategies from PLG to enterprise readiness. Easy migration, no credit card required.
Pros and Cons
- Provides comprehensive authentication, authorization, and full self-serve account management capabilities within an app.
- Offers a versatile and easy-to-integrate user management solution.
- Offers excellent security-first mindset and infrastructure, including information security management system (ISMS), multi-region, multi-geo, and up to 99.99% uptime.
- No pricing information is given.
- The number and types of integrations with other systems do not appear to be mentioned.
- No information is given about the learning curve for using the platform.

#10
WatchGuard AuthPoint
Product Description
AuthPoint multi-factor authentication (MFA) provides the security you need to protect identities, assets, accounts, and information. Try it now.
Pros and Cons
- AuthPoint MFA provides an easy-to-use, cost-effective and complete multi-factor authentication solution.
- The mobile device DNA matching technology makes it difficult for attackers to clone a user's device to access protected systems.
- AuthPoint MFA can be fully managed in WatchGuard Cloud, offering hassle-free cloud-based management and configuration.
- No information is provided about the pricing structure of AuthPoint MFA, which could be a concern for businesses on a tight budget.
- There is no mention of any integrations with other security tools and technologies, which could be a limitation for businesses that use a comprehensive security stack.
- The product seems to prioritize ease of use and convenience, which may come at the cost of advanced security features that some businesses may require.
#11
SecurID
Product Description
RSA helps manage your digital risk with a range of capabilities and expertise including integrated risk management, threat detection and response and more.
Pros and Cons
- The SecurID app provides 24/7 technical support from a world-class team
- The ID Plus subscription plan offers next-gen cloud and hybrid identity platform that integrates security, flexibility, and convenience.
- RSA provides personalized and proactive customer support to help maximize availability and uptime.
- The pricing for ID Plus subscription plans may not be affordable for all users.
- RSA's products and solutions may target more enterprise-level users than small businesses or individuals.
- The app is currently available only in English and Japanese languages, which may limit its accessibility to users who speak other languages.
#12
Ping Identity
Product Description
Ping Identity helps you protect your users and every digital interaction they have while making experiences frictionless.
Pros and Cons
- Ping Identity provides frictionless experiences for users while ensuring security.
- The PingOne Cloud Platform has an impressive 99.99% uptime, ensuring continuous availability for users.
- Ping Identity has been recognized as a leader in authentication, SSO and access management for five consecutive years by Gartner.
- It's unclear what specific features and capabilities Ping Identity offers beyond seamless and secure identity management.
- There is no clear information on pricing or plans on their website, which may be a challenge for potential customers trying to evaluate whether the product is worth the investment.
- There are no customer reviews or testimonials on the website, which could be useful for potential customers trying to understand the product's effectiveness and user satisfaction.
#13
OneLogin
Product Description
Secure your workforce, customers, and partner data with our modern IAM platform at a price that works with your budget.
Pros and Cons
- OneLogin provides a range of identity and access management solutions for workforce identity, customer identity, and partner data all-in-one place.
- OneLogin has been recognized by various industry experts including KuppingerCole and Gartner Peer Insights for its access management solutions.
- OneLogin offers ease-of-implementation and fast time-to-value with its 24/7 in-house customer support, implementation, and post go-live support.
- OneLogin may not work for those who prefer not to use cloud-based access management solutions.
- OneLogin's pricing is not transparent and depends on specific requirements.
- OneLogin offers limited compatibility with some older browsers.

#14
Auth0
Product Description
Rapidly integrate authentication and authorization for web, mobile, and legacy applications so you can focus on your core business.
Pros and Cons
- Offers a range of authentication features such as multifactor authentication, machine to machine, and passwordless login, making it more secure.
- Can work with various industries, including healthcare, retail, and public sector, and can be used for B2B SaaS applications or consumer applications.
- Auth0 also offers documentation, resources, and developer support, making it easy for developers to work with the platform.
- There is no mention of the cost of using Auth0, so it is difficult to determine if it is affordable for businesses of different sizes.
- While Auth0 offers machine to machine authentication for increased security, this may not be relevant for all businesses and their specific needs.
- Although Auth0 has integrations with multiple social login options and has a focus on user experience, there might be issues with the process of incorporating rich user profiling and facilitating more transactions.
#15
Silverfort
Product Description
Silverfort extends MFA to resources that couldn’t be protected before, automates the discovery and protection of service accounts and blocks ransomware spread in real time.
Pros and Cons
- The product offers unified identity protection that extends MFA and modern identity security to any sensitive resource.
- The agentless and proxyless MFA protection feature enables protection for any device, server or application, including resources that couldn’t be protected before.
- It offers automated discovery, monitoring and conditional access policies for all service accounts, enabling ‘virtual fencing’ without requiring password rotation.
- The product seems to be more focused on enterprise-level customers, which may not be suitable for individuals or small businesses.
- There is no clear indication of the pricing model or cost of the product, which may make it difficult for potential customers to make informed decisions.
- The product may require technical expertise to set up and operate, which may make it challenging for non-technical users.
Frequently asked
questions
There is no one-size-fits-all answer for the best MFA software. Options such as Authy, LastPass, and Google Authenticator offer different features, pricing, and security levels. Evaluate your unique needs and budget before choosing the software that aligns with your requirements.
MFA software provides an additional layer of security to user accounts by requiring users to authenticate themselves through multiple factors. Benefits include improved security, reduced risk of unauthorized access, and increased protection against phishing and other cyber attacks.
The common use of multi-factor authentication (MFA) software is to add an extra layer of security to user accounts by requiring multiple forms of authentication. It enables businesses to protect sensitive data, prevent unauthorized access, comply with regulations, and mitigate security risks. It also provides features for user management, reporting, and integration with other security systems to enhance overall security posture.
When choosing multi-factor authentication (MFA) software, consider features like support for various authentication factors, ease of use, scalability, flexibility, integration options, reporting, monitoring, and customer support. These features will help you enhance security, facilitate access control, and protect your organization from unauthorized access.
Various industries use Multi-Factor Authentication (MFA) software, including finance, healthcare, government, technology, and more. MFA strengthens security by requiring users to provide multiple forms of identification to access sensitive information or systems.
The cost of multi-factor authentication (MFA) software varies based on factors like features, provider, and the number of users. It can range from free plans with limited features to monthly subscriptions starting at $1/user to $10/user or more, depending on the level of security and customization required.
Yes, there are free multi factor authentication (MFA) software tools available. Some popular options include Google Authenticator, Microsoft Authenticator, and Authy. However, these free tools may have limitations on the number of users, devices, or integrations. Paid options often offer more advanced features and support.
Multi-factor authentication software requires a moderate level of technical expertise. Users should have some knowledge of system configurations and be able to follow installation and setup instructions. However, most mfa software offers user-friendly interfaces and helpful resources to assist with any technical difficulties.
How to use this page to find the right software
Identify your needs and requirements from the software. Consider factors like functionality, features, platform compatibility, budget, and any specific industry or personal preferences.
Based on your needs, prioritize the features or functionalities that are essential for your software.
Explore the website link of each software to gather more detailed information about it.
Still not sure?
Discuss you software needs in our community of experts. Join Marketing Tribe ->
What’s next?
Learn more hacks and tricks of growing your business. Subscribe to daily dose of marketing and growth tactics and lessons. Subscribe to the Mailmodo Bulletin ->
Modernize your operations with interactivity
- 📈 Automate bills, usage reports, and notifications with the journey feature
- ⚡ Enable people to raise issues inside the emails using forms
- ✉️ Use APIs to trigger and send notification and reminder emails